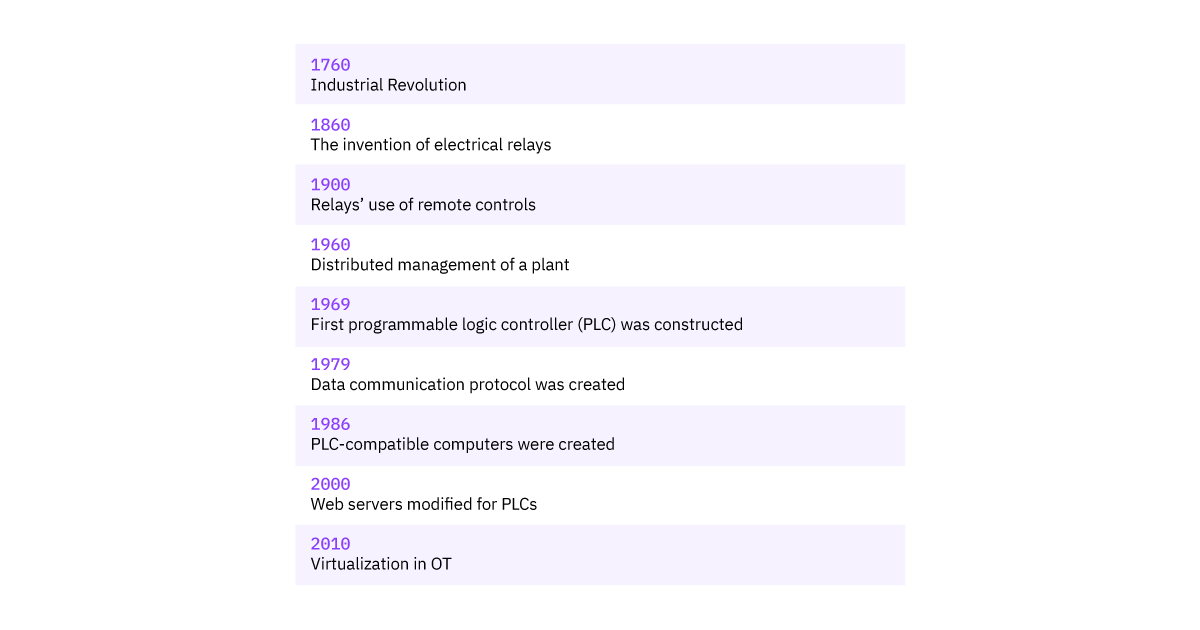
The banking sector is significantly behind in terms of cloud technology adoption. While these difficulties affect all companies, regulated areas such as financial services face particularly complex terrain. And their difficulties need specific problem-solving.
Financial services businesses must face three challengings, and overlapping difficulties to effectively upgrade their IT:
- Outdated legacy technology
- Cybersecurity risks
- New working styles and employee expectations
The good news is that, with the important approach to IT modernization, financial businesses of all sizes can meet industry change, hybrid work needs, cybersecurity, and compliance. The journey starts in the cloud.
This does not indicate that businesses must make the transition all at once; in fact, some organizations are banned from doing so in more regulated areas of the industry. However, almost all financial services businesses can take concrete, powerful steps today to adopt a more dynamic IT posture and prepare for the business and regulatory environments of the future.
By going deeper into the challenges to IT modernization, financial services businesses can understand how to overcome them (while being compliant) and thrive in the new world of work.
Challenge 1 in Financial Services: Outdated Legacy Technology
Many financial services organizations depend on systems that have been cobbled together over years, if not decades. This technology debt can make even the most simple new technologies more difficult to implement, while also reducing their capacity to satisfy changing customer and staff needs.
More specifically, the financial services industry tends to struggle with quickly onboarding new employees and providing ongoing support, enabling hybrid employees with the tools they require wherever they are, and troubleshooting and updating current systems rather than focusing on higher-value activities.
Even delaying IT modernization can be helpful. Businesses can (finally) begin supporting microservices, APIs, and DevOps by moving parts of their business to the cloud. By allowing businesses to build new locations more quickly, merge branches, introduce a new product or service offerings more quickly, and accelerate the time to value from major changes like mergers, acquisitions, and divestitures, doing so helps businesses become more flexible. By taking these actions, IT troubleshooting can be minimized, freeing up technical personnel to focus on higher-value tasks.
Financial institutions can start to reduce the technical debt produced by legacy systems and start to develop an organizational culture that attracts and keeps talent by moving some tasks to the cloud.
Challenge 2 in Financial Services: Cybersecurity Risks
The financial services industry is flooded with data, including data on customers, businesses, employees, and trade. All of this information must be protected, but it also needs to be available when and where it is needed. Organizations that lack a strong security architecture run a higher risk of accidentally losing data or experiencing hacker attacks.
New technologies and new thinking are needed to address an expanded and deeper assault surface. Due to the transition to a mixed work style, many employees usually access the network using their devices. Data needs to be secured and encrypted as it moves from its starting point to its finishing point. Businesses must also follow compliance rules without sacrificing their objectives.
To adapt to this situation, the financial services sector should use zero trust best practices, ensuring that staff members have access to the information and tools they need, whenever and whatever they work. Financial services companies can more effectively protect sensitive information, improve corporate security, adhere to compliance regulations, and minimize their audit footprint by securing sensitive apps and data on-premises or in public cloud platforms. Adopting zero trust allows enterprises to further strengthen security and compliance by encrypting data in motion, containerizing and deleting data from mobile devices, limiting data sharing and copying, and carefully dividing protected data.
These IT advancements also have a business case. Enhancing data protection, enabling quick recovery from security disasters, and promoting business continuity will lower risk and improve resilience. It is not only morally right but also essential to protect data everywhere.
Challenge 3 in Financial Services: New Working Styles and Employee Expectations
Employees don’t necessarily have different needs from those of on-premise employees just because they may work from home or on a mixed schedule. Whether using a personal device or a corporate-owned, personally enabled (COPE) device, relationship managers, personal bankers, roaming branch staff, and loan agents must be able to access their applications, information, and data on a single aggregated workspace without compromising sensitive client or personal information. Customers demand greater security and reduced friction at all points of service.
The most knowledgeable financial services workers are aware of how to reduce risk through diversification and flexibility. It’s the same for IT leaders who assess and put into practice sensible and clever IT strategies. Banks may more easily provision and manage employee resources in any place with the use of desktop as a service, or DaaS. This makes it possible to roll out new goods and solutions for both customers and employees with ease in the future. They can also easily adjust to changing needs and improve IT processes.
The financial services industry can protect distributed workers, apps, devices, and networks even as workstyles and expectations evolve by using a more flexible, resilient security model.
IT Modernization
IT modernization is not a one-and-done effort, nor is modernizing enterprise technology — or creating the infrastructure to enable it — a minimal expense in the banking sector, as it is in any company. However, if done strategically and with a view toward the future, IT modernization may be easy, safe, effective, and, yes, inexpensive. An estimated 1.95% increase in overall sales comes from a 1% increase in innovation spending.
Businesses can deliver the cutting-edge, adaptable experiences that both customers and employees need while keeping the agility required to succeed in today’s quickly changing market. Everyone can feel optimistic about that.
Here at CourseMonster, we know how hard it may be to find the right time and funds for training. We provide effective training programs that enable you to select the training option that best meets the demands of your company.
For more information, please get in touch with one of our course advisers today or contact us at training@coursemonster.com