With the development of remote work, modern organizations must prioritize compliance and...
Why Can’t We Avoid Operational Technology Security?

Any hardware and software that directly monitors and controls industrial equipment and all of its assets, processes, and events to detect or trigger a change is considered operational technology (OT). Despite its important element in a wide range of critical industries, OT security is also especially vulnerable to assault.
Attacks against operational technology systems have caused disastrous work interruptions and physical damage in sectors all over the world, from power grids to nuclear reactors. However, cyberattacks on OT targets have increased significantly, with attackers most usually targeting the manufacturing industry.
It is apparent that more steps must be taken to improve the standard of OT security. Important infrastructure operators must understand the important role of OT, the threats posed by threat actors, and how to build a secure OT architecture.
The Scope of operational technology
Mining, construction, oil and gas transmissions, electricity and utilities, chemical plants, water treatment, industrial machinery, and transportation are just a few of the industries that rely on operational technology. Operational technology settings include industrial networks, industrial control systems (ICS), and operation and maintenance activities.
The information technology (IT) revolution started well before the OT revolution. In fact, OT has been around since the start of the Industrial Revolution.
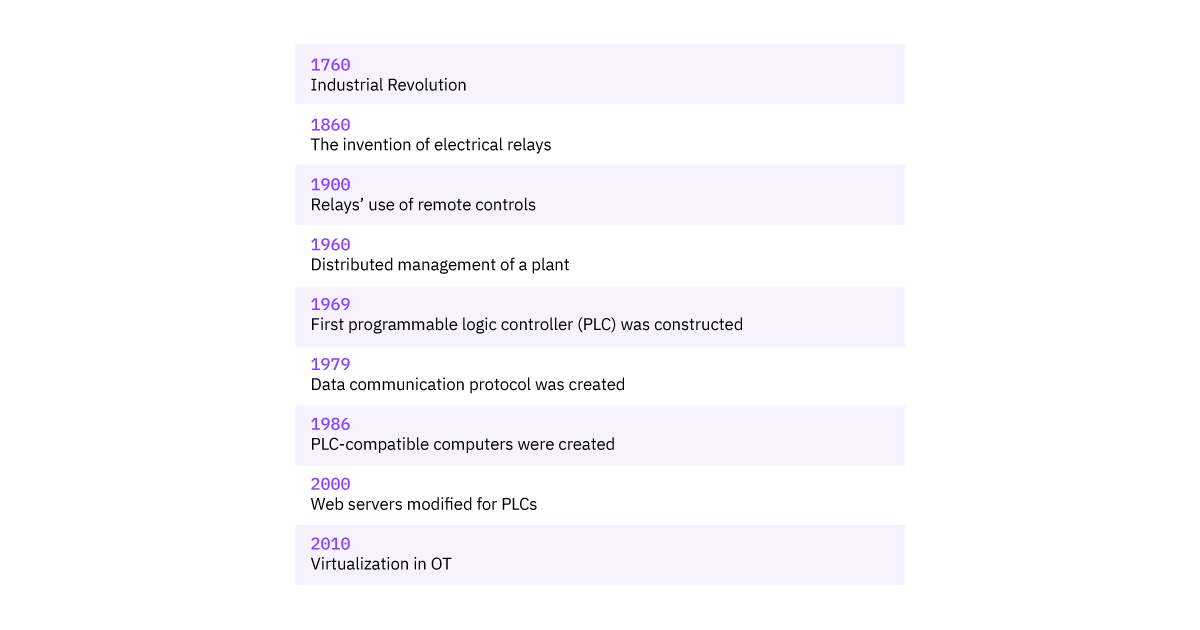
In What Ways Do OT and IT Differ?
IT is the processing of digital data using computer systems to support company operations such as marketing, sales, customer relationship management, communications, and so on. Typical IT systems include your email server, web server, enterprise resource planning system, voice-over-IP phone, print server, and helpdesk application.
OT manages the operation of physical processes and machines, whereas companies utilize computer systems to monitor and control industrial and technological operations.
IT applications and procedures aid in the control of the OT sector, which includes power generation and transmission, water treatment, and chemical manufacture. Endpoints controlled in OT, on the other hand, are usually physical assets such as motors, conveyors, valves, and forklifts. These “things” come in a variety of sizes, shapes, sophistication levels, versions, and vintages.
In short, OT includes all systems that deal with the physical transformation of products and services. They are mission-critical task-specific systems that are also industry-specific.
In terms of security, OT suppliers use annual patches as part of their system security strategy. Many businesses must rely exclusively on OT vendors for security assistance because of a lack of product understanding and a complex environment.
Common Components of Operational Technology
ICS assets are included in the digital equipment utilized in industrial processes. This covers many areas of manufacturing, similar applications, and infrastructure systems such as power grids and water treatment facilities.
The key ICS elements that combine to create OT that interacts with the physical environment are supervisory control and data acquisition (SCADA) and distributed control systems (DCS).
All major ICS components are listed below:
- SCADA systems collect data from sensors, which are usually located in dispersed places, and send it to a centralized computer for management and control.
- DCS is an automated control system made up of control units that are geographically spread throughout the plant or control area.
- A programmable logic controller (PLC) is an industrial computer control system that analyzes the condition of input devices continuously and decides how to regulate output devices based on a custom program.
- RTUs are microprocessor-based devices that monitor and manage field equipment while communicating with SCADA or plant control systems.
- Human-machine interface (HMI) is a device or software program function that allows people to engage and communicate with machines.
- A process history database (PHD) is a program that collects, keeps, and replays data from previous and ongoing plant processes. When used in conjunction with other industrial software programs, it improves process performance and data security, allowing for faster and better decisions.
Operational Technology Protocols
Operational technology protocols are proprietary and vendor-dependent because they are often closed systems. Different methods are used at different stages of the Purdue model. OT devices and systems have increasingly adopted IT-standard network protocols such as TCP/IP to simplify operations and increase interoperability with older IT hardware. Modbus is a communication protocol that is commonly used in all PLCs, irrespective of vendor.
The following are a few OT protocols:
- Modbus
- MelsecNet
- DALI
- DSI
- Dynet
- Obix
- ZigBee
- xAP
- DNP3
- M-Bus
- INSTEON
- BACAnet
- EnOcean
An Increase in Operational Technology Security Challenges
For more than a decade, there has been an increase in cyberattacks on businesses with OT environments and systems, especially with the integration of OT and IT. The adoption of the industrial internet has also increased the risk of disruptive threats to OT systems, which exist for all internet-connected devices.
Although OT systems are integral components of important manufacturing and production equipment assets, they have previously been excluded from security plans.
Convergence of IT and OT increases attack surfaces:
- Credentials are not secure. Operators have been using weak passwords to get easy access to networks. As a result, hackers can easily gain operator access without authorization by employing brute-force password attacks.
- User accounts that are defaulted/shared. Operators have access to both the same ID and the same default credentials for devices if a secure solution is not in place.
- Equipment from the past. Endpoint tool coverage is further limited by vendor restrictions and legacy equipment.
- Security expertise. New networking technologies necessitate the use of updated skills in OT industrial situations. It is important to fill the knowledge gap in OT security.
- Limited abilities. Threats are always changing, and tactics are improving. Many exploits are caused by a lack of OT cybersecurity skills and understanding.
- The operating system is outdated. Security risks can enter an outdated operating system that isn’t receiving security updates. To avoid compromise, every piece of equipment must be quantified and patched by the manufacturer’s specifications.
- Vulnerable protocols. Many manufacturers are creating secure solutions to currently unprotected protocols and equipment by including features like authentication and encryption.
- Security posture Security has traditionally paid minimal attention to the industrial computing community. In terms of security standards and processes, as well as collaboration with outside security researchers, the OT industry falls significantly behind the IT business.
Significant Operational Technology Cyberattacks
Vital OT systems’ digitization has created some concerns. Additionally, there are now even more dangers and risks as a result of ICSs being connected to the internet.
Each of the following cyberattacks had a major effect on OT systems:
Ukrainian Power Grid Attack, 2015
Threat actors assaulted the Ukrainian electricity grid in December 2015. As a result, 230,000 people had power outages that might last up to six hours. Thirty substations were disconnected for three hours as a result of the attack on the SCADA and computer systems of the power grid. The attacker had been present in the victim’s infrastructure for more than six months.
A spear-phishing campaign was launched against system administrators and IT staff who worked for several electricity distribution companies around Ukraine in the months leading up to the attack.
BlackEnergy first gained attention in 2014 due to how usually it was used to hack into energy companies. Its objective was to gather data on the networks and infrastructure in preparation for future cyberattacks.
In this case, when victims opened an Excel attachment in a malicious email, a BlackEnergy malware variant started to run. For several months, threat actors remotely controlled the BlackEnergy virus to gather data, travel between hosts, discover security holes, enter the OT network, and perform further “reconnaissance” tasks.
The SCADA systems were taken over by malicious actors who started remotely turning off substations during the attack. The attack deleted files on servers and workstations using the KillDisk virus. The uninterruptible power supply, modems, remote terminal units, and commutators were already turned off.
Stuxnet Worm, 2010
Stuxnet was one of the most advanced malware programs ever made. The goal of this malware was to physically harm the centrifuges of the Natanz nuclear power plant in Iran.
Targeting SCADA systems and PLCs, which allow the automation of electromechanical operations like those needed to manage machinery and industrial processes, Stuxnet is said to have seriously affected Iran’s nuclear program.
Stuxnet malware was believed to have infected the Natanz facility network via an infected USB drive. To move throughout the network unnoticed, Stuxnet used some “zero-day” bugs, stolen certificates, and default access credentials.
Malicious function blocks were inserted into the targeted PLC by the malware once it had identified the hardware and the operational conditions. The purpose of this function block was to accelerate the spin rate of the centrifuges at predetermined intervals, therefore effectively inducing parts to fail and ultimately causing the machines to self-destruct.
Triton Malware, 2017
The first malware, dubbed Triton, focused exclusively on protecting critical infrastructure facilities from serious physical harm and maybe life-threatening accidents. This malware targeted a Saudi Arabian petrochemical industry and interfered with its safety precautions.
The Triton malware could infect the safety instrumented systems within the complex. These systems are vulnerable to remote control once the malware was deployed. Had the attackers disabled or modified them before using other software to make plant equipment malfunction, the results would have been disastrous.
Norsk Hydro (LockerGoga) Ransomware, 2019
The ransomware program known as LockerGoga, which significantly affected Norsk Hydro, a Norwegian producer of aluminum, is a recent example of how quickly ransomware attacks are changing.
First, early versions of LockerGoga encrypted the files and other data on infected systems. The malware then showed a message to victims asking them to pay a ransom to receive the decryption keys. Additionally, more recent versions of the malware also can forcibly log victims off of an infected system and prevent them from getting access back.
The manufacturer had to switch to manual procedures at multiple locations as a result of the attack. As a result, the production systems for Norsk Hydro’s extruded solution group suffered significant damage, requiring temporary plant closures and operating slowdowns. Although Norsk Hydro quickly responded, the damage was extensive. All of the company’s employees—more than 35,000 workers working across the global operations of the aluminum massive attack by the LockerGoga malware.
Common Attack Vectors
Technologies and techniques are utilized to monitor and control real-world events, processes, and objects as part of OT security solutions. These technologies also help to protect assets, information, and people. OT cybersecurity should be part of a comprehensive risk management strategy that also includes disaster recovery and traditional physical security.
Organizations must be aware of the most common attack vectors for malicious assaults to secure their networks against unauthorized access. An attack vector is a strategy or approach that an attacker takes to reach the intended target.
Below are the common types of cyberattack vectors:
- Removable media. A USB flash drive or comparable internal data transfer device has the potential to introduce malware onto a system.
- Compromised equipment. There could be weak points in the supply chain’s equipment. The firmware of the device might be changed during the transition.
- Unauthorized connections. Mobile devices, laptops, and computers are examples of linked endpoint devices that can be attacked.
- Remote access. A system with remote access may be hacked by an attacker to access a network or device.
- Exploit unpatched vulnerabilities. An unpatched vulnerability in an application or operating system could allow attackers to carry out actions they are not authorized to or inherit the permissions of other users.
- Phishing. This traditional vector method is widely used. Phishing is a type of social engineering that includes taking the identity of a reliable person or organization to attack the victim and obtain sensitive or essential information.
- Weak credentials. Because of weak passwords and password reuse, credential exposure acts as a conduit for initial attacker access and lateral migration. Recent malware assaults, like Mirai, have taken advantage of managed devices’ and IoT-connected devices’ weak credentials.
Best Practices For OT Solutions
Organizations classify and prioritize cybersecurity controls in different ways. The following security technologies are used by OT security solutions:
- Risk assessment
- Compliance and standards
- Inventory management
- Network security
- Vulnerability management
- Security information and event management
- Malware protection
- Defense in depth
- Access control
Organizations must ensure that their OT is backed by a strong framework of rules, procedures, and guidelines to strengthen their cybersecurity posture and achieve best-practice cybersecurity requirements. Best practices for OT cybersecurity include the following examples:
- Analyzing GAPs and risks to determine the maturity level of OT security and reporting any issues that need to be resolved
- Creating a roadmap and strategy that are created specifically to the client’s needs and the environment to increase the maturity
- Making a comprehensive plan for the hardening and security of the most valuable operational assets
- Creating and building incident response playbooks and use cases for security operations center (SOC) for OT-specific attacks by MITRE’s ATT&CK for the ICS framework
- OT application integration with cyber threats and tools
- Logically and physically limiting access to the ICS network and its devices
- Avoiding unauthorized data tampering and protecting particular ICS components from attack.
OT Security Cannot Be Ignored
Operators of critical infrastructure need to be more proactive when it comes to IT/OT convergence. For the company to advance, a thorough cybersecurity plan that takes into account every stage of the organization’s security lifecycle is required.
In summary, creating an efficient OT cybersecurity framework provides complete support for the entire enterprise. These suggestions address a variety of topics, including governance, risk management, system development and commissioning, document protection, incident response, and disaster recovery.
To reduce the risks posed by unsecured OT, businesses will need to implement a combination of IT cybersecurity products and services with specialized, OT-specific cybersecurity solutions.
Want to know more about Cybersecurity? Visit our course now.
Here at CourseMonster, we know how hard it may be to find the right time and funds for training. We provide effective training programs that enable you to select the training option that best meets the demands of your company.
For more information, please get in touch with one of our course advisers today or contact us at training@coursemonster.com
