04.23.2024
Why You Should Take Power BI Classes

Posted by Marbenz Antonio on February 6, 2023

“Hardening” as a software concept is a widely used term, but the actual meaning of the practice and its importance for modern IT organizations is not frequently discussed. Hardening is essential for all organizations, even those that utilize specific STIGs or configuration guides.
Hardening is the act of minimizing a system’s vulnerability to attacks, thus improving its overall security. This can be achieved by disabling or eliminating unneeded features or functions, and operating the system with more limitations than its default settings. Another approach might be limiting or completely removing the privileges of a component to access features (such as APIs or files) of another component, ensuring only authorized components are used.

STIGs serve as a basic guideline for strengthening a system’s security. DISA STIGs are designed to be repetitive and focus on a single product instead of an integrated system, making assumptions about external systems, business processes, and non-technical controls that may not be accurate. The instructions in STIGs are intended to be straightforward for the implementor, usually, a system owner or technical administrator, who is presumed to have a limited understanding of the target product or the security consequences of the controls being implemented. STIGs are written in clear and straightforward language to minimize confusion during application or audit, but exceptions may be necessary if deviations occur.
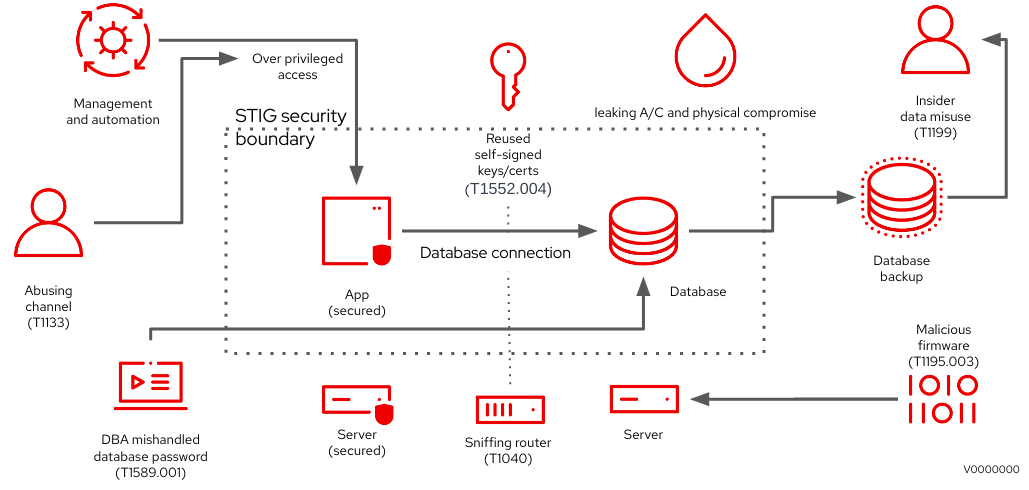
The concept of hardening is a critical aspect of ensuring the security of an IT system. While STIGs offer guidelines as a starting point for system hardening, they concentrate on a single product rather than an integrated system and have numerous implicit assumptions about external systems, business procedures, and non-technical controls. STIGs are meant to be straightforward instructions for the implementor, typically a system owner or technical administrator, and are written in simple terms. However, the ever-evolving landscape of software threats and vulnerabilities means that more needs to be done to ensure security beyond the STIGs. To keep up with these threats, software vendors like Red Hat offer services that help determine which vulnerabilities apply to a system, but deep product expertise is still necessary to fully understand a product’s attack surface. By combining this expertise with other guidance from sources like NIST’s Secure Software Development Framework or OWASP guidelines, suppliers like Red Hat can provide default hardening guidance. This guidance can then be tailored by end-users to meet their specific hardening requirements based on historical attack patterns they have experienced, with the help of documentation in the form of deployment and security guides.
Hardening helps in enhancing the security posture of a system by reducing its attack surface. This is achieved by disabling or removing unnecessary features and functions, limiting privileges, or restricting access to certain system components. The goal of hardening is to limit the opportunities for exploitation, prevent unauthorized changes, reduce the number of active services, and minimize the potential for lasting damage in case of a successful attack. By implementing hardening principles, such as logging and monitoring, it becomes easier to detect security threats or compromises and prevent data breaches.
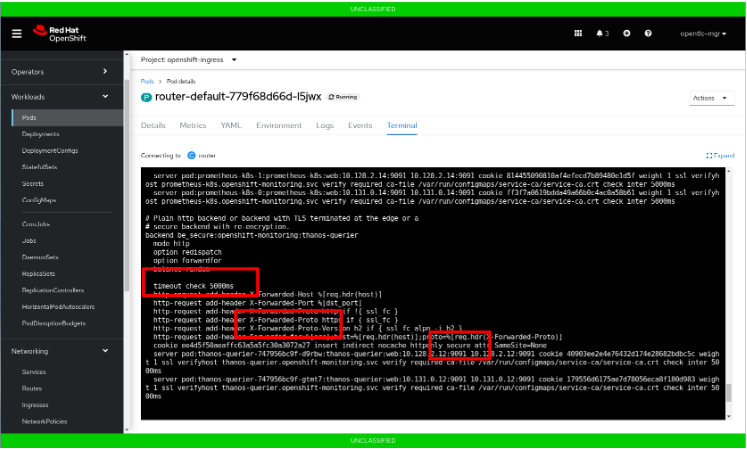
Hardening plays a crucial role in enhancing the security of a system. Adherence to specific guidelines from organizations, such as the use of DISA’s STIGs by DoD entities, can ensure that the system meets IT security standards and complies with industry regulations, thus providing confidence to system owners that their systems are secure.
Here at CourseMonster, we know how hard it may be to find the right time and funds for training. We provide effective training programs that enable you to select the training option that best meets the demands of your company.
For more information, please get in touch with one of our course advisers today or contact us at training@coursemonster.com
