At Microsoft Security, they are aware of the difficulties in protecting your data, which is your...
Microsoft Priva Subject Rights Requests Simplify Privacy Protection

The General Data Protection Regulation (GDPR) comes into place in 2018 and created a new standard for the level of control European Union citizens have over the personal data they shared online. Since then, the number of privacy rules has grown around the world, influencing the privacy landscape we see today. According to Gartner®, by the end of 2024, three-quarters of the world’s population will have current privacy regulations covering their data. Today, additional laws such as the California Consumer Privacy Act (CCPA) and Brazil’s Lei Geral de Proteço de Dados (LGPD) empower people to exercise their right to request the personal data that organizations have collected from them, including Microsoft Priva Subject Rights.
Responding to subject rights requests allows organizations to meet regulatory requirements while giving people control over their data. Although responding to requests can be complicated, Microsoft Priva Subject Rights Requests can help ease the process—and with the previewed arrival of Right to be Forgotten, Priva Subject Rights Requests can help organizations further support how they respect the privacy of their customers and employees.
Understanding how people think about privacy
As many businesses throughout the world change their privacy policies, having both tools to address privacy regulations and a good understanding of how consumers perceive and feel about privacy is critical to enabling customer trust. Vasu Jakkal, Corporate Vice President of Microsoft Security, Compliance, and Identity, introduced Microsoft Priva, the brand category for Microsoft Security, at Microsoft Ignite in 2021. Priva reaffirmed its commitment to assist organizations on their privacy journey by developing tools that help safeguard personal data and manage subject rights requests at scale. Organizations must have systems in place to manage their privacy, but it is also important to have a thorough understanding of how individuals think about privacy to influence their policies. Microsoft just commissioned privacy research that investigates the emotional textures of privacy as well as what causes privacy vulnerability. They discovered that when businesses empathize with people’s privacy issues and address them clearly, they develop trust and differentiate themselves from competitors.
Businesses need to analyze the different reasons for privacy risks for both their customers and their business. A customer, for example, may feel concerned or helpless if they do not know how their data is being used. However, if customers are given information about how their data is being used and clear options for data control, their concerns may be eased and faith in the process earned. A business’s privacy vulnerability could show as a lack of transparency or basic compliance, allowing privacy risks to possibly unfold. For example, a company that serves a data subject request ineffectively or with minimal effort may be managing its privacy at a vulnerable level. If the company adopted a “beyond-compliance,” human-centered privacy approach, it may provide policies that help it build privacy resilience, allowing it to differentiate itself from competitors while earning customer trust.
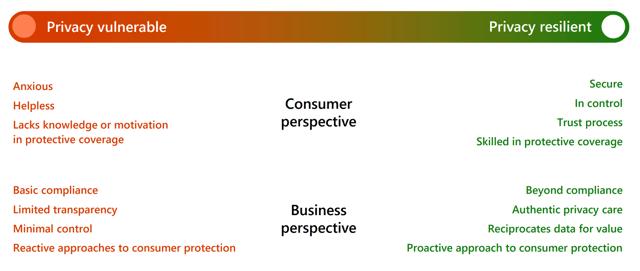
Figure 1. The differing perspectives of consumers and businesses regarding privacy vulnerability versus privacy resilience.
The graph above depicts a privacy spectral range from vulnerable to resilient, with customer and business perspectives included. On the customer side, it can range from feeling worried, helpless, and lacking knowledge or motivation in protective coverage to feeling secure, in charge, trusting the process, and knowledgeable about protective coverage. It extends from basic compliance, limited transparency, minimal control, and reactive approaches to beyond compliance, real privacy care, reciprocating data for value, and a proactive approach to consumer protection.
Microsoft Priva Subject Rights Requests can help
Even when a company is dedicated to a positive approach to privacy, managing and responding to subject rights requests can be a time-consuming and difficult procedure. It can be exceedingly time-consuming and taxing because they are also time-bound, adding to the organization’s complexity. Responding to these requests usually takes extensive collaboration and manual review, and even delivering a single request can be costly. Nonetheless, satisfying these requests is not just a legal requirement, but also a visible manner of showing respect for customer and employee privacy.
Priva helps enterprises manage requests at scale more efficiently—Priva Subject Rights Requests automates the search and gathering of content related to the data subject and simplifies processes such as in-line review, redaction, and collaboration, all from a simple dashboard. Admins can get started quickly by using request templates, which allow them to construct requests with recommended default options. They can also use Microsoft Power Automate integration and API support to better fit into their existing processes.
Want to know more about Microsoft? Visit our course now.

Figure 2. Priva Subject Rights Requests overview dashboard showing insights.
Priva Subject Rights Requests help admins in meeting the strict deadlines connected with rules such as GDPR while also easing the administrative load of time-consuming processes such as collection, review, and redaction. Completing a request usually requires collaboration from multiple areas inside the company. Priva offers secure collaboration via Microsoft Teams and maintains a history tab, highlighting activities made by all contributors for easy auditing—streamlining the complexity of requests from start to finish.
Microsoft Priva Subject Rights Requests highlights:
- Automates discovery: Gathers personal information from the requestor and discovers data conflicts such as sensitive information or data of other users.
- In-place review and secure collaboration: Review files in their native views, redact in-line with built-in tools, and consolidate collaboration within a secure platform.
- Ecosystem integration: Integrates with an organization’s existing workflow to manage requests throughout the digital estate in a consistent manner. Priva Subject Rights Requests are integrated with in-house or partner-built privacy solutions via the Microsoft Graph subject rights requests API.
The newest Priva Subject Rights Requests update, Right to be Forgotten, is here
The Right to be Forgotten is included in both the GDPR and the CCPA, giving people the opportunity to seek the deletion of all information an organization has gathered about them, with a few stated exceptions that allow data retention. For example, a former employee in an EU-based company believes she left personal data-containing documents on SharePoint. The employee can use her right to personal data by submitting a subject rights request for deletion to the business. As Priva Subject Rights Requests evolve, they are excited to announce the preview release of Right to be Forgotten, which will help organizations in meeting requests such as the employee’s desire for deletion.
With this new feature, admins can now select delete as a request type, or get started with the delete template and get purpose-built flows that help surface conflicts and streamline deletion—leveraging the Microsoft retention and deletion platform and working better together with teams already using data lifecycle management and records management. This feature will also allow admins the ability to choose various approvers for each request and, once the workflow is complete, access to the reports tab where they can check their summary report and review results.

Figure 3. Delete request in the approval stage, showcasing approver details and the complete approval button.
Here at CourseMonster, we know how hard it may be to find the right time and funds for training. We provide effective training programs that enable you to select the training option that best meets the demands of your company.
For more information, please get in touch with one of our course advisers today or contact us at training@coursemonster.com
