Access your IBM Cloud Resources by Using a Client-to-Site VPN

Who wants to keep their VPN stack when a fully managed client-to-site VPN is so simple to provision?
This article is a follow-up to one IBM published two years ago titled “Access Virtual Servers in a Virtual Private Cloud with OpenVPN,” in which they described how to install and set up OpenVPN to access your VPC resources. Since then, Client-to-Site VPN for VPC has become a new, fully managed alternative, removing the need for you to set up and operate your own OpenVPN server.
With client-to-site connectivity provided by the client VPN for VPC, remote devices can securely connect to the VPC network using an OpenVPN software client. This solution is helpful for telecommuters who want to establish a secure connection to the IBM Cloud from a distant location, such as a home office.
In this article, IBM describes how to deploy, provision, and configure a client VPN for a VPC using Terraform. You can find the source code and directions for deploying a fully operational example of this architecture on GitHub. They’ll give a high-level summary of the procedures, all of which make use of Terraform to simplify provisioning and configuration:
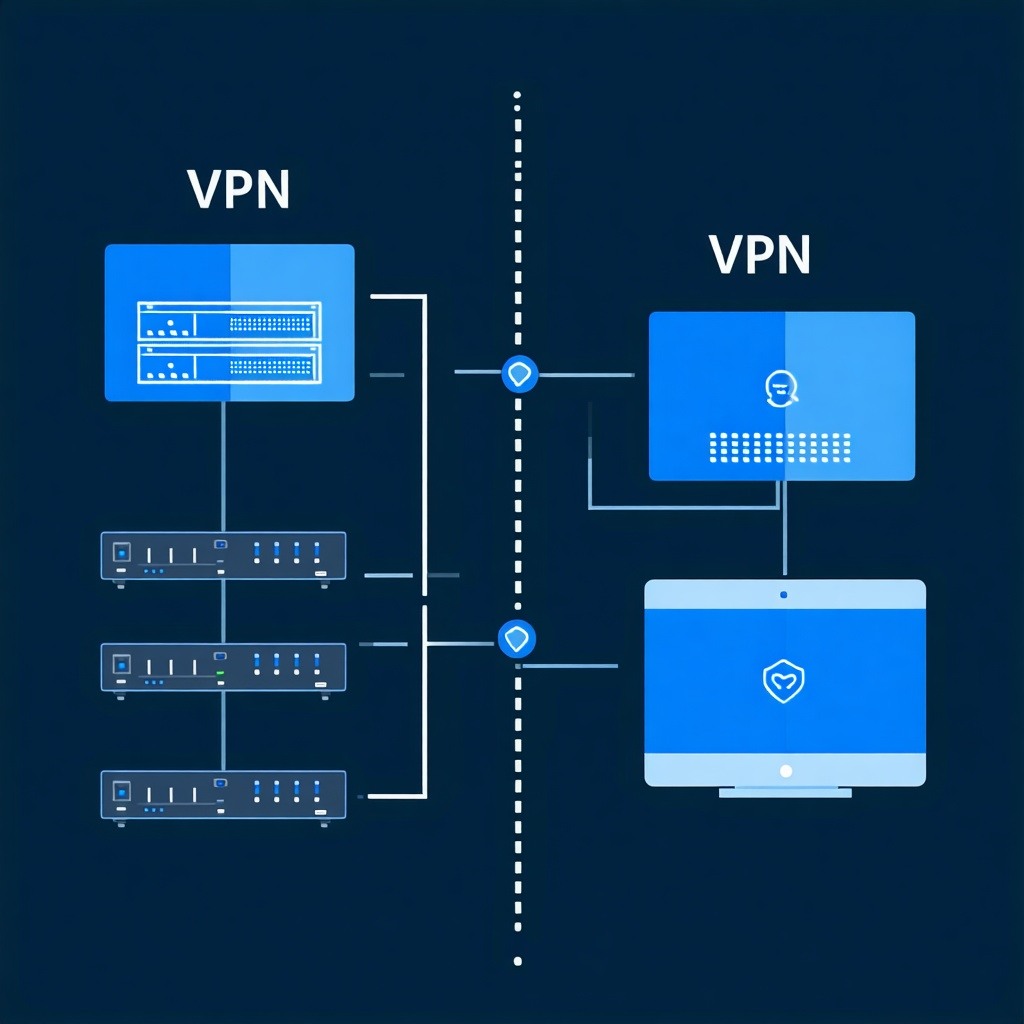
These features are a part of the architecture shown above:
- The client and server certificates used by Client VPN for VPC are stored using IBM Cloud Secrets Manager.
- During its initialization, the Client VPN for VPC retrieves the certificates from Secrets Manager.
- A connection is made by the user to the Client VPN for VPC. An IP address is assigned to the PC from the VPN IP pool.
- From there, if the appropriate routing configuration has been set in Client VPN for VPC, the user can connect to VSI in VPC or Classic.
Step 1: Prepare the Client VPN for VPC configuration
Making the server and client certificates that Client-to-Site VPN for VPC will use is the first step. The product documentation includes all the instructions. Included are the following:
- Create client and server certificates.
- Keep the certificates in Secrets Manager as secrets.
- Access these secrets by giving Client VPN for VPC an IAM authorization.
These two files—generate.tf and secrets.tf—do this in Terraform:
Step 2: Provision Client VPN for VPC
IBM may provision the Client-to-Site VPN for VPC once the certificates have been created. It needs a VPC and a subnet, at the very least. A standalone mode (great for testing) and a high availability deployment are supported by Client VPN for VPC. They’ll test the capability using the standalone deployment:
- In vpc.tf, the VPC and subnet are created. The security group rules for SSH, DNS, and reaching private endpoints are pre-installed when they are created.
- In vpn.tf, the Client VPN for VPC is created. To enable SSH connectivity between the hosts connecting to the VPN and the hosts in the cloud, it includes a security group. The VPN uses UDP on port 443 and has a public domain name once it has been created.
- As part of the Terraform provisioning, an OpenVPN configuration file is created. It can be used to connect to the Client VPN for the VPC server using the OpenVPN client:
Step 3: Test connectivity with other virtual server instances in VPC and Classic
You can then test the minimum needed connectivity to cloud service endpoints. To complete our connectivity testing, IBM can provision one virtual server instance in VPC and one in Classic, both connected via Transit Gateway:
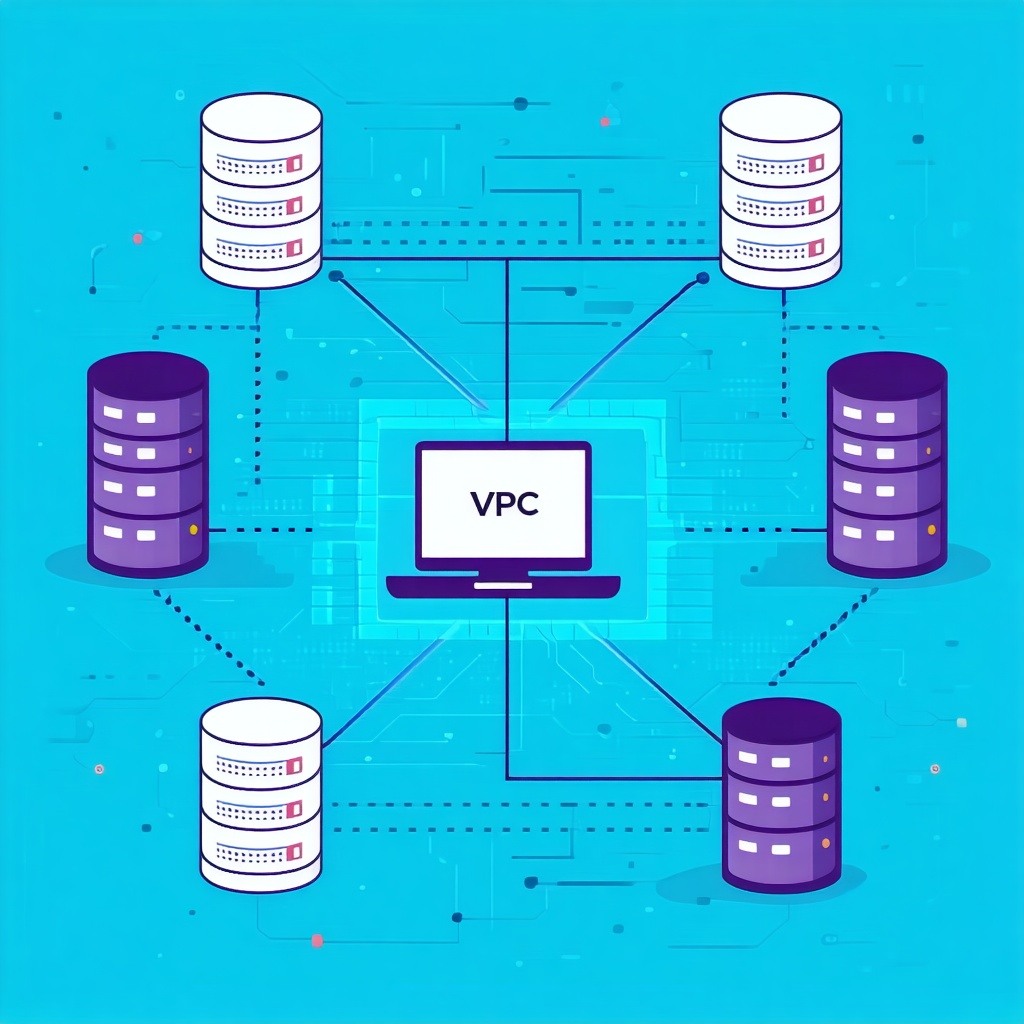
The following can be seen in the picture above:
- Client VPN for VPC used to connect OpenVPN to IBM Cloud.
- a ping to the endpoint for the Watson Speech to Text cloud service.
- a private network connection made securely to a VSI in classic infrastructure.
- a private network connection made securely to a VSI in a VPC.+
Want to know more about IBM Cloud? Visit our course now.
Here at CourseMonster, we know how hard it may be to find the right time and funds for training. We provide effective training programs that enable you to select the training option that best meets the demands of your company.
For more information, please get in touch with one of our course advisers today or contact us at training@coursemonster.com




Comments ()