The Truth about Scrum Job Titles and Scrum Roles - Course Monster Blog
Learn why the three scrum positions (scrum master, product owner, and development team) are more like job titles than job descriptions.
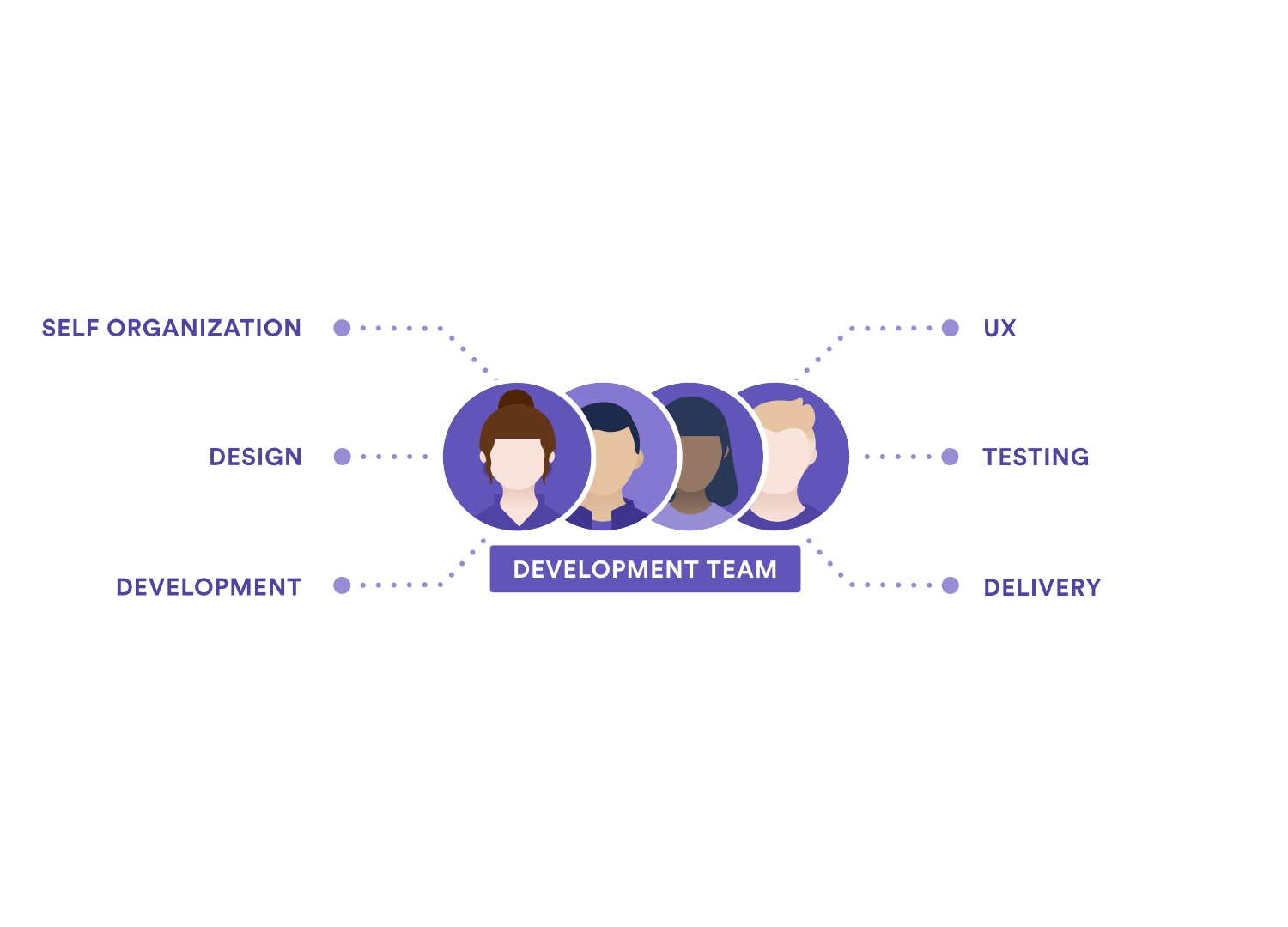
What are the 3 Scrum Roles?
Product owner, scrum master, and development team members are the three positions in Scrum. While this is fairly obvious, determining what to do

