Is Monitoring the Dark Web Worth It? - Course Monster Blog

The Dark Web is a section of the internet that allows its users to remain anonymous. Unfortunately, this anonymity allows buyers and sellers to swap their content. Credit cards, medical records, personal information, user credentials, and more horrible data sets are offered here in cybersecurity. To maintain anonymity, cryptocurrency is commonly used as a payment mechanism.
Consider the Dark Web to be a retail center or mall. The ground floor is open to the public for browsing and shopping. The stores range from department stores to thrift shops and do not offer any specialized items or services. More specialized stores can be found on the mall’s upper floor, but you must be a member to enter. This affiliation is founded on trust, commerce, and credibility. Access is limited, but it is possible. Elite and premium stores are the next level up. These are not accessible by elevator or escalator, and entry is by invitation only.
The point is that the dark web is not easily accessible to the average internet user, and keeping an eye on what is going on is not a one-person job. This is why corporations hire specialized services to scan the dark web for critical information about them.
What are Dark Web Scanning Services?
The number of dark web monitoring services has increased tremendously in recent years, but are they worthwhile? What are the facts of this service, and why do some businesses believe it provides them with a false feeling of security?
Many businesses now provide Dark Web monitoring services, but there is widespread misunderstanding about how they work or whether they work at all. The following are examples of dark web monitoring:
- Scanning services – every day, hundreds of thousands of hidden websites are scanned for information on your company.
- Trading services – where they will trade on your behalf to verify data, obtain insights, or buy your data Banks, for example, may purchase credit cards issued by them in order to cancel them.
- Collaborating services – discussing attack prospects, zero-day exploits, and intelligence sharing on forums
Do you think multiple services are worthwhile now that you’ve learned about them? Here’s what you should know.
What Is the Quality of Dark Web Scanning Services?
Despite some providers’ excellent marketing campaigns, you should be aware that none of them can scan the entire Dark Web, which is an impossible operation. In reality, they will search the most widely available databases (with over 8 billion entries), which often contain outdated data, which is often an accumulation of earlier breach data sets. They are less likely to scan forums that are exclusively accessible to trusted individuals, and they are extremely unlikely to do a deep web scan where peer-to-peer trade occurs. If you intend to utilize them, keep in mind that they will monitor and report on publicly available information, not delete it.
 Usually, they will provide a gateway via which to access useful administration tools for customizing scan criteria and reporting. These interfaces are useful, but they only provide insights into what they can, not the entire Dark Web.
Usually, they will provide a gateway via which to access useful administration tools for customizing scan criteria and reporting. These interfaces are useful, but they only provide insights into what they can, not the entire Dark Web.
When something ends up on an underground site, the alternatives for removing it are restricted. Some dark web dealers may offer to remove it after you pay, but can you really believe them?
The reality is that they will not. After all, you’re dealing with shady people with corrupted values who are only interested in profit and don’t care about the harm they cause.
Do You Need Dark Web Trading Services?
This is invariably where the real action takes place. It’s been lucky to deal with people that have the knowledge and existing networks to provide this service. In this experience, the number of people who can function in this field is little in comparison to generalists.
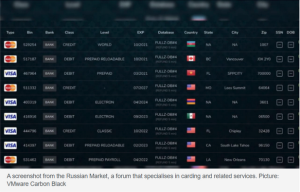 Individuals with this expertise are typically reformed hackers, police enforcement, military, and intelligence officials. The challenge you have here, and this is the value system, is that if a person has acquired the trust of the inner sanctum of the clandestine trading floors, they have done so through questionable activities. As a result, You find it difficult to think they have the necessary fundamental integrity. You’ve seen examples when trade analysts behave as double agents, switching sides depending on who pays the most, and issues where they function as both a buyer and a seller on the same transaction.
Individuals with this expertise are typically reformed hackers, police enforcement, military, and intelligence officials. The challenge you have here, and this is the value system, is that if a person has acquired the trust of the inner sanctum of the clandestine trading floors, they have done so through questionable activities. As a result, You find it difficult to think they have the necessary fundamental integrity. You’ve seen examples when trade analysts behave as double agents, switching sides depending on who pays the most, and issues where they function as both a buyer and a seller on the same transaction.
5 Best Practices for Dark Web Monitoring Services
- Qualify hardAsk a lot of inquiries to find out if they are a tech company offering an intricate search feature or if they have agents inside these communities. Inquire how many search analysts they have, how many languages are spoken in their team, where the analysts are located, how they obtain insights, have they registered their services with police and intelligence teams, and can they show you examples of forums in which they participate.
- TestRun a 90-day trial instead of a complete subscription to assess the integrity of their skills. If they are only conducting an automatic search and not a manual analyst-driven effort, you should consider other possibilities.
- Legal protectionMake sure you have legal protection, including protections for improper behavior.
- Be smart
Never provide the agents with sensitive PII to search on, such as your birth date, bank account information, secret keys, and so on. Accept the possibility that anything you share will be sold. - Use Open-Source Intelligence (OSINT) Tools firstNumerous OSINT tools can be used directly to deliver priceless insights. Begin with these, and then examine whether you have any intelligence gaps.
Is Dark Web Monitoring Worth It?
So, to answer the original question, is it worthwhile?
The answer is a qualified yes, provided you have realistic expectations, have examined their capabilities, and do not believe the hype around monitoring services. Dark web monitoring would be part of my cyber program, but it would be low on my priority list. It is preferable to invest in preventative solutions rather than reactive ones like this. You are in a better position to begin if you have established a Zero-Trust security architecture, extended detection and response (XDR), multi-cloud protection, and DLP.
Remember what you learned many years ago when you submitted your first dark web monitoring report at a Board Meeting: “what do you want me to do about this?” ”. You immediately realized that any reporting approach must be accompanied by action; else, the report is just hype.
Before investing significant resources in this service, it is recommended that you focus on making your data set as dark web dull as possible, such as:
- Delete non-essential data from your network — it astounds me how much needless data we keep, such as outdated resumes that we only used once and no longer require.
- Challenge data sharing with third parties and ensure they have adequate security in place.
- Encrypt sensitive data at rest and in transit – personally identifiable information, credit cards, medical information, and so on.
- Keep credit cards off your network on PCI-compliant servers.
- Have business systems in place to detect fraudulent behavior as fast as possible, such as offshore transactions on gift cards/credit cards, dormant cards, chargebacks, and so on.
- Concentrate on effective user awareness education rather than just training. Personally, get down with your business teams and coach them on best practices, as well as build cyber champions in the organization.
Here at CourseMonster, we know how hard it may be to find the right time and funds for training. We provide effective training programs that enable you to select the training option that best meets the demands of your company.
For more information, please get in touch with one of our course advisers today or contact us at training@coursemonster.com




Comments ()